TM
Virtual Components for the Converging World
Amphion continues to expand its family of application-specific cores
1
See http://www.amphion.com for a current list of products
CS5310/11/12
Standard Hash Algorithm (SHA-1 & SHA-2)
Cores
The CS5310/11/12 Hashing Cores are designed to achieve data authentication in digital broadband, wireless, and
multimedia systems. These high performance application specific silicon cores support the Secure Hash
Algorithm as described in the NIST Draft Federal Information Processing Standard 180-2 (DFIPS 180-2 "Secure
Hash Standard"). The CS5310 core offers SHA-1 algorithm that is required for use with the Digital Signature
Algorithm (DSA), as specified in the Digital Signature Standard (DSS) and provides authentication between
users during data transmission. The CS5311 core provides SHA-256 algorithm and offers a security equivalent to
128-bit AES. The CS5312 offers the entire SHA-2 algorithms including SHA-256, SHA-384, and SHA-512. These
cores are available for both ASIC and programmable logic versions that have been hand crafted by Amphion to
deliver high performance while minimizing power consumption and silicon area.
CORE FEATURES
Table 1: CS5210/11/12Secure Hash Algorithm Cores at a Glance
SHA-1
SHA-2
FEATURES
CS5310
CS5311
CS5312
Fully implements
SHA-1
secure hash algorithms to NIST FIPS 180-2
specifications
�
Fully implements
SHA-256
secure hash algorithms to NIST FIPS 180-2
specifications
�
Fully implements
SHA-256, SHA-384, SHA-512
secure hash algo-
rithms to NIST FIPS 180-2 specifications
�
High Speed operation
�
�
�
Each 512-bit block requires 81 master clock cycles (1 clock per algo-
rithm step + 1 clock load)
�
Each 512-bit block for SHA-256 requires 65 master clock cycles (1 clock
per algorithm step + 1 clock load)
�
�
Each 1024-bit block for SHA-384 and SHA-512 requires 81 master clock
cycles (1 clock per algorithm step + 1 clock load)
�
32-bit I/O interface
�
�
64-bit I/O interface
�
Supports user input initialization vectors
�
�
�
Supports message padding
�
�
�
HMACs (Hashing Message Authentication Codes) efficiently supported
�
�
�
Simple external interface
�
�
�
2
CS5310/11/12
Standard Hash Algortihm (SHA-1 & SHA-2) Cores
APPLICATIONS
Electronic financial transactions
-
E-Commerce
-
Banking
-
Securities exchange
-
Point-of-Sale
Secure corporate communications
-
Storage Area Networks (SAN)
-
Virtual Private Networks (VPN)
-
Video conferencing
-
Voice services
Personal mobile communications
-
Video phones
-
PDA
-
Point-to-Point Wireless
-
Wearable computers
Secure environments
-
Satellite communications
-
Surveillance systems
-
Network appliances
.
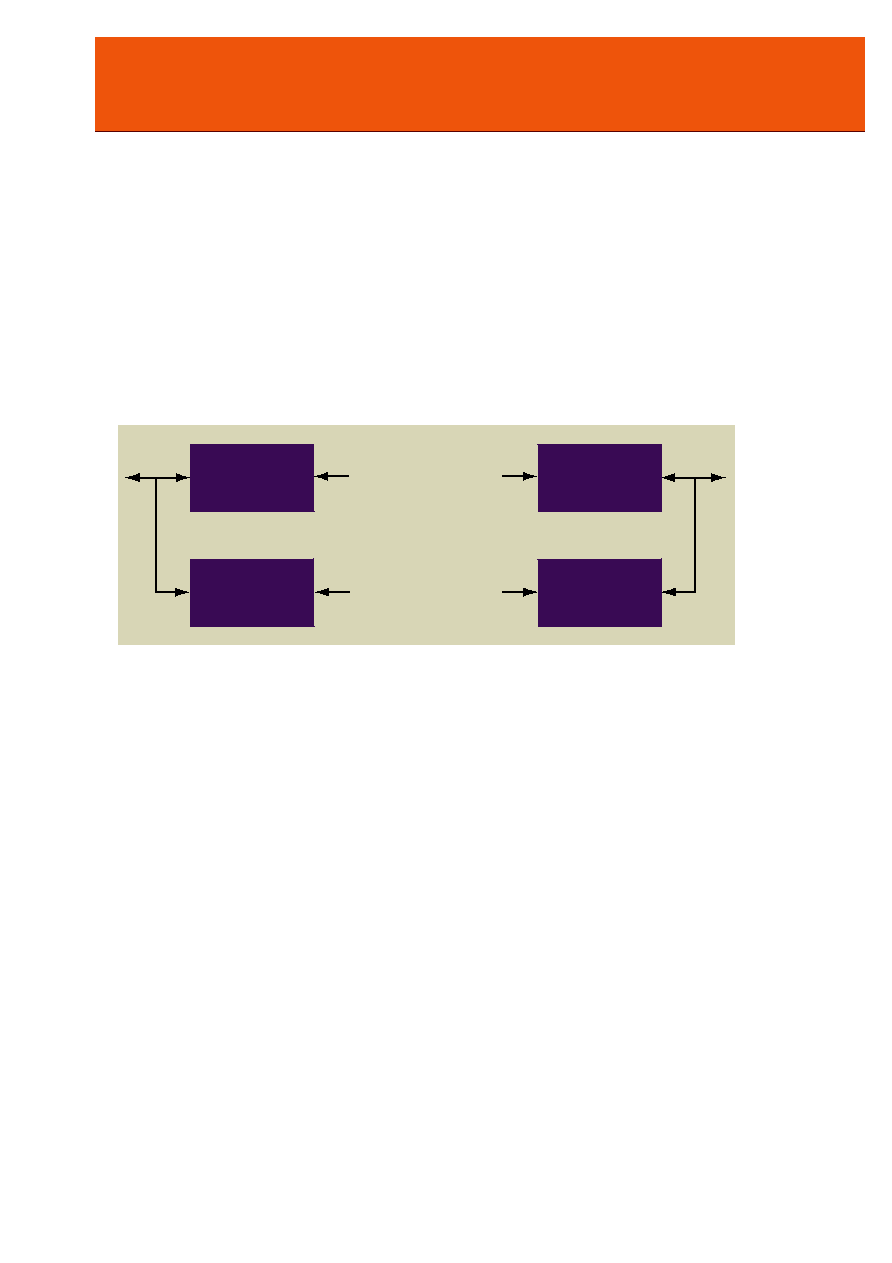
Figure 1: Example of an Authenticated Encryption System Using 3DES or AES with Matching SHA Algorithm
3DES
or
AES
HMAC-SHA-1
or
HMAC-SHA-2
3DES
or
AES
HMAC-SHA-1
or
HMAC-SHA-2
Confidential data
transmission over
insecure medium
MAC transmission
over insecure
medium
Data
Data
3
TM
CS5310 SHA-1 CORE
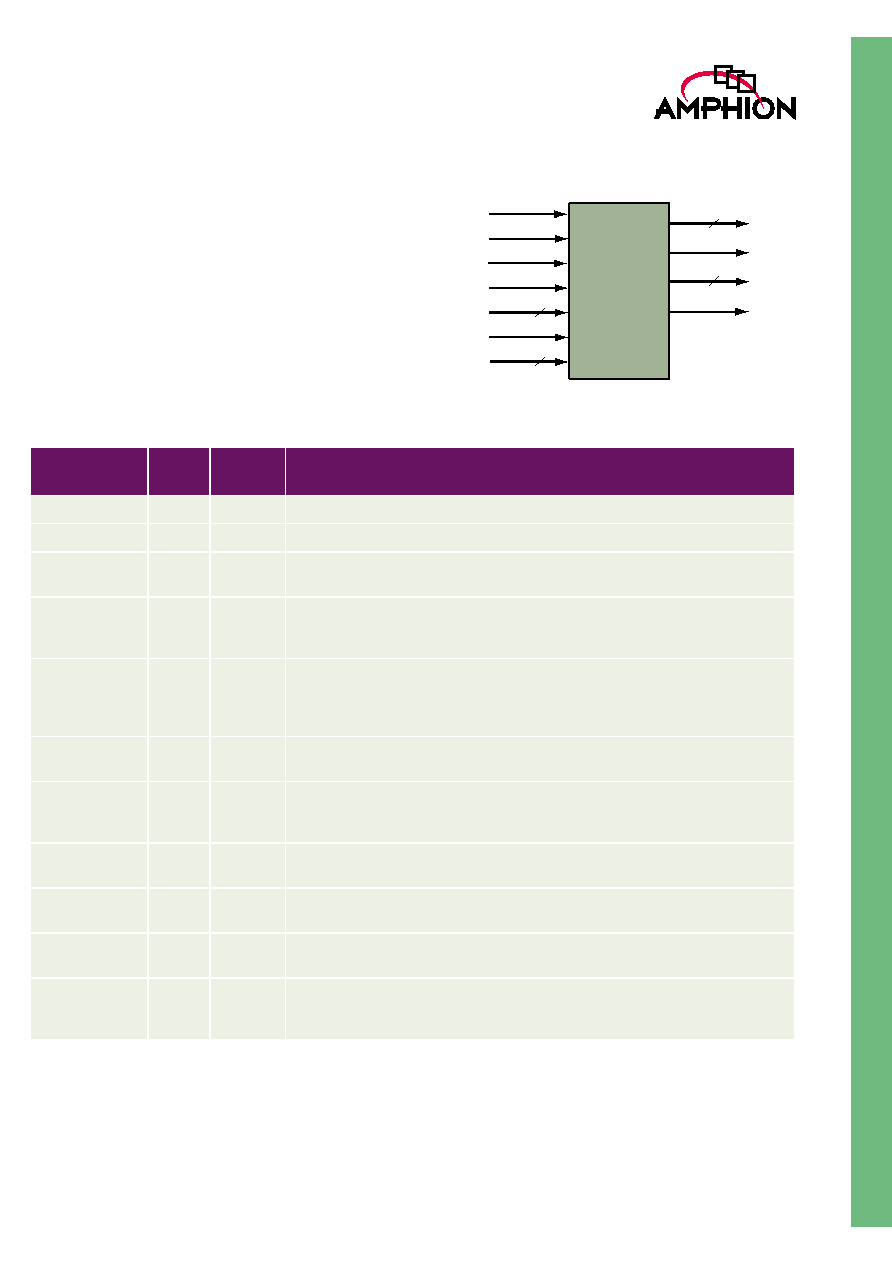
SYMBOL AND PIN DESCRIPTION
Table 2 describes the input and output ports (shown
graphically in Figure 2) of the SHA-1 core. Unless otherwise
stated, all signals are active high and bit (0) is the least
significant bit.
Figure 2: CS5310 Symbol
CS5310
SHA-1
QRDY
Q
QADDR
DRDY
DNUMB
D
DLAST
IV
LOAD
CLK
RST
32
3
32
5
Table 2: CS5310 Signal Interface Signal Definitions
Signal
I/O
Width
(Bits)
Description
CLK
Input
1
System clock signal, all flip-flops within the core are triggered on the rising edge
RST
Input
1
Asynchronous global reset signal, active HIGH.
LOAD
Input
1
Input data port D is sampled on the rising edge of CLK when LOAD is asserted.
Otherwise the port is ignored
IV
Input
1
Initialization vector flag. Asserting this flag denotes that the data presently sampled
is the core initialization vector, otherwise the sample is considered as message
data. This port is ignored when Load is deasserted.
D
Input
32
32-bit data input port sampled on the rising edge of CLK when Load is asserted.
When IV is deasserted this is processed as message data beginning with the most
significant word of a 512 bit block, when IV is asserted the data is processed as an
initialization vector
DLAST
Input
1
When asserted, the data present at port D, sampled at the rising edge of CLK is
flagged as being the last in the current input block.
DNUMB
Input
5
The value present at DNUMB denotes how many bits of the data at D are to be
sampled as message data when DLAST is simultaneously asserted to denote the
last word in a block. Ignored when DLAST is deasserted.
Q
Output
32
Message digest output port driven on the rising edge of signal CLK, most significant
32 bits of 512 bit block presented first
QRDY
Output
1
Message digest ready signal, driven on the rising edge of CLK, when asserted signi-
fies the message digest for the current block is present at output port Q
QADDR
Output
3
Denotes the significance or address of the 32 bits of the message digest present
simultaneously a output port Q
DRDY
Output
1
Data input ready signal, when asserted denotes that the core is ready to accept
data (or initialization vectors) placed on port D, when deasserted denotes the core is
busy and the input data stream must be stalled.
4
CS5310/11/12
Standard Hash Algortihm (SHA-1 & SHA-2) Cores
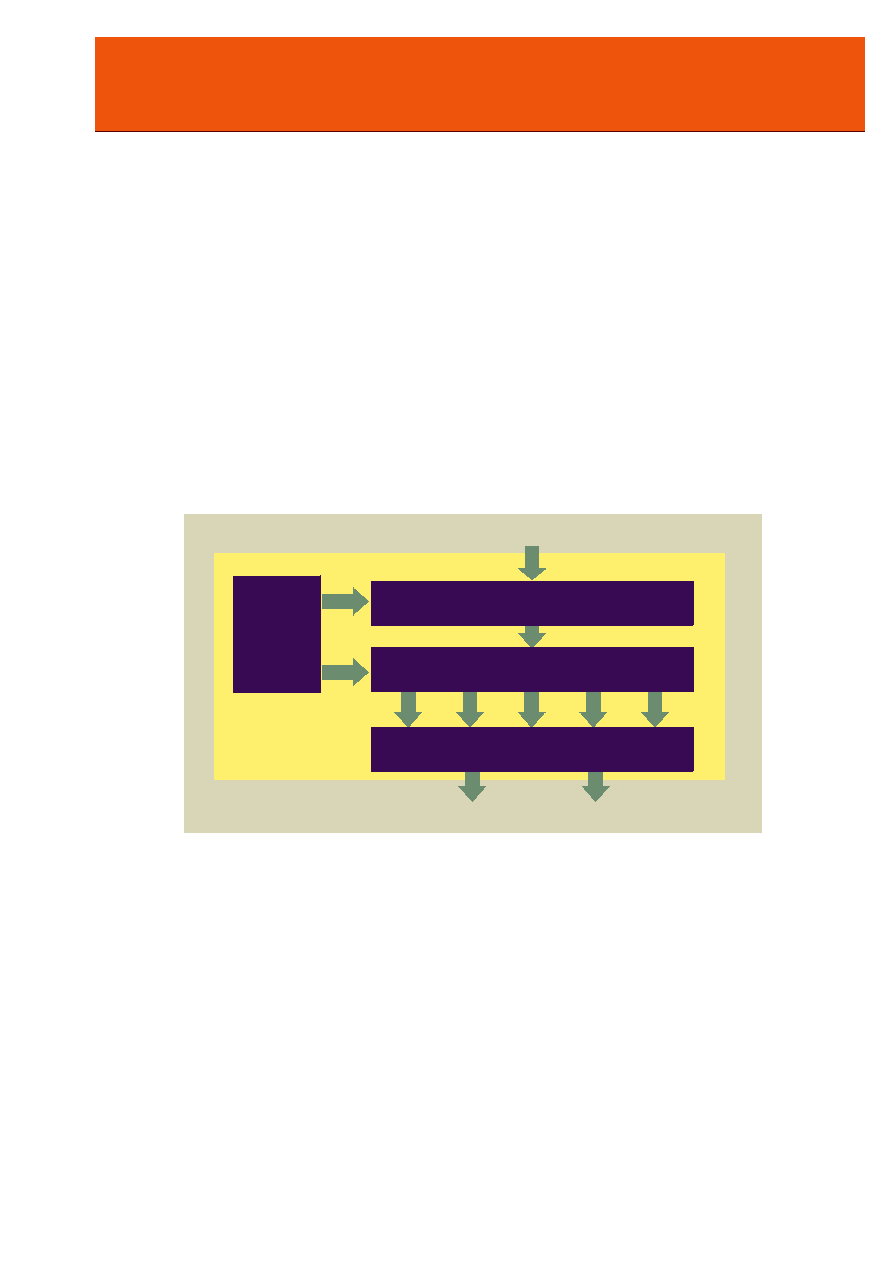
FUNCTIONAL DESCRIPTION
SHA-1 algorithm is used by both the transmitter and the
intended receiver of a message in computing and verifying a
digital signature. SHA-1 produces a 160-bit condensed
representation of the message called a message digest. The
message digest is used to generate a signature for the
message. SHA-1 is also used to verify any received signature.
Any change to the message in transit will result in a different
message digest, and the signature will fail to verify. Figure 3
represents the functional block diagram of CS5310 core.
The SHA-1 algorithm processes an input message, of length
n*512 bits, in successive 512-bit blocks to produce a 160-bit
message digest. The message digest is transmitted to the
receiver along with the message and verified, thus providing
authentication and ensuring the message has not been altered
or interfered with. It consists of four rounds of processing
each of 20 steps. Once all 80 processing steps are complete,
five 32-bit intermediate variables are updated and the next
message block is processed. Once processing of the last
message block is complete the final variable values represent
the 160-bit message digest.
Optionally, prior to loading the first message word the
external logic may load customized initial values into the core.
This allows pre-computed initial values to be used for efficient
implementation of a Hash-based Message Authentication
Code (HMAC).
The Amphion CS5310 core is an excellent complement to the
Amphion CS5210-40 suite of DES/Triple DES cores.
Figure 3: Block Diagram of the CS5310 SHA-1 Core
Data Input
Control
5 32-bit
words
Data Buffer
SHA Rounds
Output Buffer
Q Address
Q Output
5
TM
CS5311 SHA-256 CORE
SYMBOL AND PIN DESCRIPTION
Table 3 describes the input and output ports (shown
graphically in Figure 4) of the SHA-256 core. Unless otherwise
stated, all signals are active high and bit (0) is the least
significant bit.
Figure 4: CS5311 Symbol
CS5311
SHA-256
QSTRB
DSTAT
QADDR
Q
DNUMB
D
DLAST
IV
LOAD
CLK
RST
Table 3: CS5311 SHA-256 Core Interface Signal Definitions
Signal
I/O
Width
(Bits)
Description
CLK
Input
2
System clock, rising edge active
RST
Input
1
Asynchronous reset
LOAD
Input
1
Load input message data
IV
Input
1
Load input initialization vector.
IV should be asserted with LOAD when an initialization vector is to be loaded prior
to hashing a message.
D
Input
32
Input message vector
DLAST
Input
1
Input last message data word
Should be asserted when loading last word of message to enable SHA padding
operations
DNUMB
Input
5
Input data word validity
This signal is ignored unless DLAST is asserted. DNUMB indicates the number of
valid bits contained in the last message word.
Q
Output
32
Output data port
DSTAT
Output
1
Input port status
Indicates the readiness of the input interface to accept new message data. When
asserted, initialization vectors and data words may be loaded.
QSTRB
Output
1
Output data strobe. Asserted to indicate valid data on the output data port.
QADDR
Output
3
Output data address. Indicates the relative address of the output data words, 0:
most significant word of hash data.




